Secure your Shared Access Signature (SAS) in Azure Storage by using Stored Access Policy (SAP). A Stored Access Policy defines access rights and restrictions. This policy can then be used to create Shared Access Signatures that can be used by clients.
An inherent benefit of using Stored Access Policy is that the Shared Access Signature can be revoked anytime by deleting the underlying Stored Access Policy. Without using Stored Access Policy, the user may not be able to revoke a given Shared Access Signature, which may have an impact on the security of the Azure Storage account.
Stored Access Policy is a much safer option. Without the use of Stored Access Policy, the only way to revoke the Shared Access Signature is to regenerate the account key. This may also have an adverse impact on existing applications that rely on Shared Access Signature tokens generated with the account keys.
A better option would be to create a Stored Access Policy for each container and create Shared Access Signature based on the Stored Access Policy. If Shared Access Signature is ever compromised, the underlying Stored Access Policy can be deleted to keep the account safe.
Create Shared Access Signature based on Stored Access Policy
Here is how to create a Shared Access Signature key using Stored Access Policy.
- Go to Azure Portal
- Go to the storage account.
- Go to the container where you want to apply this policy.
- Select Access Policy from the menu.
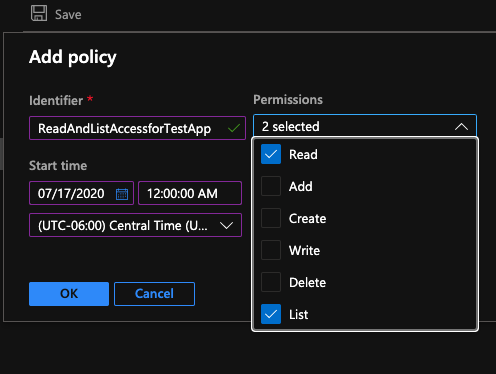
- Create a new Stored Access Policy. Be sure to set the expiration date, and the permissions based on the requirements. Limit the permissions to only the ones that you absolutely need.
- Now go back to the storage account, and select Storage Explorer (preview).
- Select the Blob where the Stored Access Policy was applied.
- Right-click and Select Get Shared Access Signature.
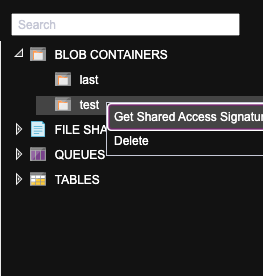
- From the Access Policy dropdown select the Stored Access Policy configured earlier.
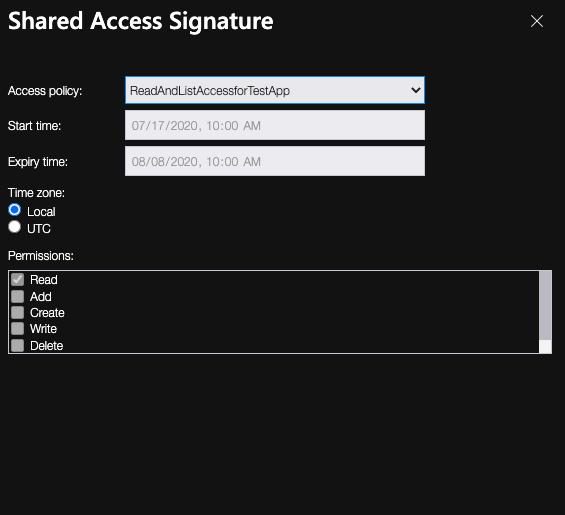
Keep the Shared Access Signature secure and use Azure Vault or other similar services, to limit the exposure even further.